What is a firewall?
A firewall is a network security-related tool whose main purpose is to monitor incoming and outgoing network communications and report that some of them have crossed or been blocked based on a specific set of safety rules. The Firewalls create a barrier between dominated and trusted internal networks between untrustworthy outside the network, such as the Internet. Firewall explanation in Arabic
Firewalls can be hardware, software, or both. Firewalls prevent unauthorized Internet users from accessing the private networks connected to the Internet, especially the internal Internet networks known as the Intranet. All incoming or outgoing network connections via the private network must pass through the firewall for the purpose of checking and ensuring that they are free of any harmful content and thus allow their passage and block the harmful ones that do not comply with the specified security standards. That is, the firewall is a filter and filter.
Firewalls are based on the following types
Software Firewalls :
These programs are designed to protect the computer by blocking some programs from sending and receiving information from the local network or the Internet. A famous example of a firewall program is the Windows Firewall, which comes integrated with the Windows operating program from Windows.
Hardware Firewalls :
This hardware is found on most Network Routers and can be set up via the Router Setup Screen. An example of this equipment is ZyWEL from ZyWALL, which is a standard security gateway that comes with a firewall and other security specifications.
How does a firewall work?
The firewall analyzes incoming data traffic based on predetermined rules as mentioned previously and filters out incoming data traffic from unsecured or questionable sources in order to prevent attacks. Firewalls protect data traffic at the data entry point of a computer, which is called the Port, at which information is exchanged with external devices. For example Source address 172.18.1.1 is allowed to reach destination 172.18.2.1 via carrier 22.
It is more like homes and rooms. Considering that the IP addresses are homes and carriers are the rooms in the house, where only trusted people (source addresses) are allowed to enter the house (the target address) and then they have purified again so that people in the house are allowed only to enter specific rooms (target carriers) Depending on whether they are homeowners, children or guests. The homeowner is allowed to enter any room (that is, a carrier) while children and guests only enter specific rooms (specific buses).
Types of firewalls
1- Proxy Firewall :
It is an old type of firewall. The Proxy Firewall acts as a gateway entry between a network and another for a specific application. Proxy servers can provide additional functions such as Content Caching as well as security by preventing direct connections from outside the network. This type can affect production capabilities and the applications it supports.
2- Stateful Inspection Firewall :
This means the inspection firewall and this type is considered as a “traditional” firewall. This type of firewall permits or blocks traffic or data traffic based on status, carrier, protocol. He monitors all activities from the first moment of the initiation of the call until it is closed and makes the decisions of liquidation based on the rules determined by the manager as well as the “context”. The context is the use of information from previous communications and packets belonging to the same connection.
3- UTM Firewall :
This acronym refers to Unified Threat Management and means unified management to deal with threats. The UTM firewall usually combines the functionality of an inspection firewall with antivirus programs. It may include some additional services such as cloud services management. UTM Firewalls focus on simplicity and ease of use.
4- Next-generation Firewall :
This means the future firewall. This type is referred to as NGFW, which is advanced firewalls that are not only for filtering packages or for status inspection. Most companies employ these advanced types of firewalls to block recent threats such as advanced malware and application attacks. These types of firewalls must include:
- Standard firewall capabilities as status inspection.
- Integrated intrusion prevention capability
- Awareness and control of the application to see and block dangerous applications and behaviors
- Upgrade tracks and feed them with future information
- Technology to address escalating security threats
How much is firewall software :
There are a lot of companies in the market with different names of their firewall products. Of course, a hardware-based firewall is expensive than the software-based. It depends on the need for what type of you looking for.
All product varies on the requirements like Home small office SMB Enterprise businesses. Prices are different for all vendors.
Read also, UnBlocked games at school and play safely the complete guide to bypass firewall.
Best firewall application
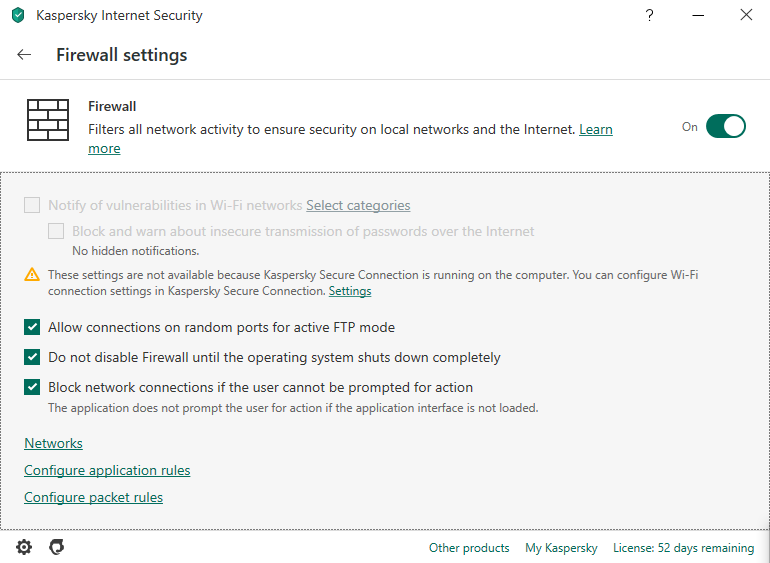
We will discuss here Kaspersky Internet security
Kaspersky: There are many products made by this company are available at kaspersky.com. But I love their Internet Security – very user friendly and easy to configure firewall rules.